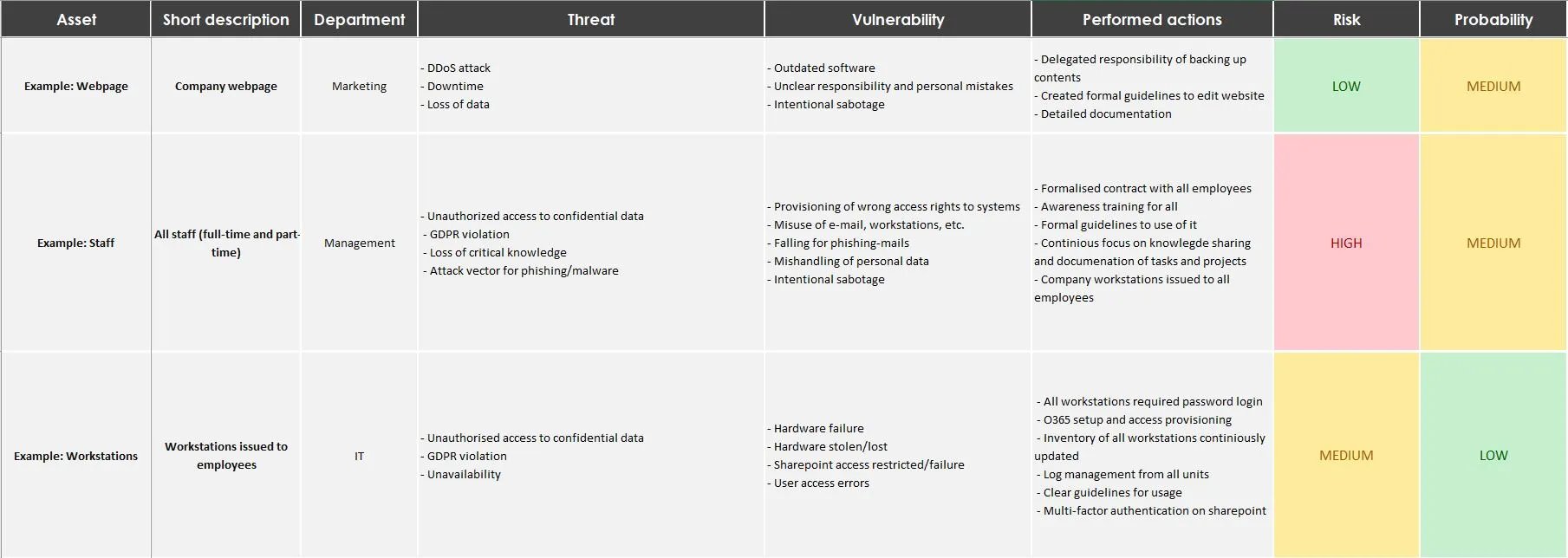
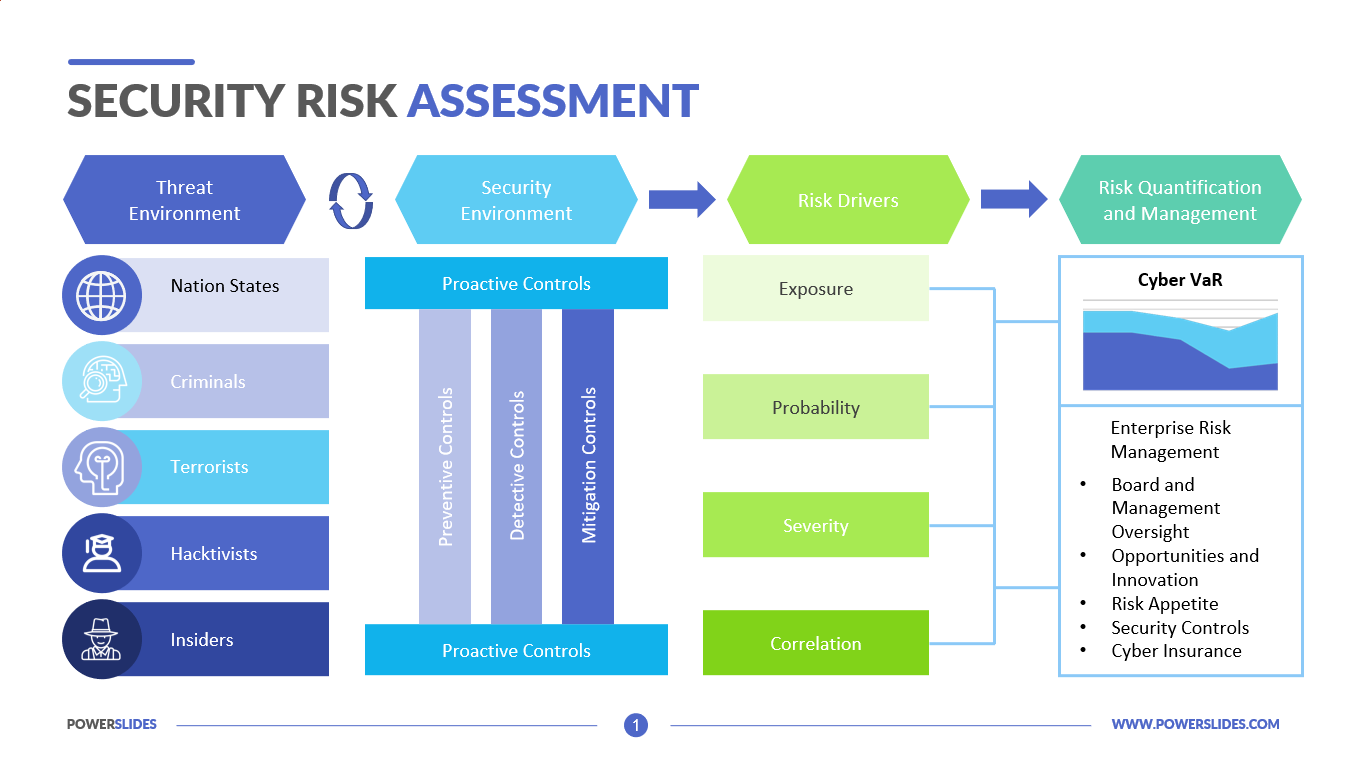
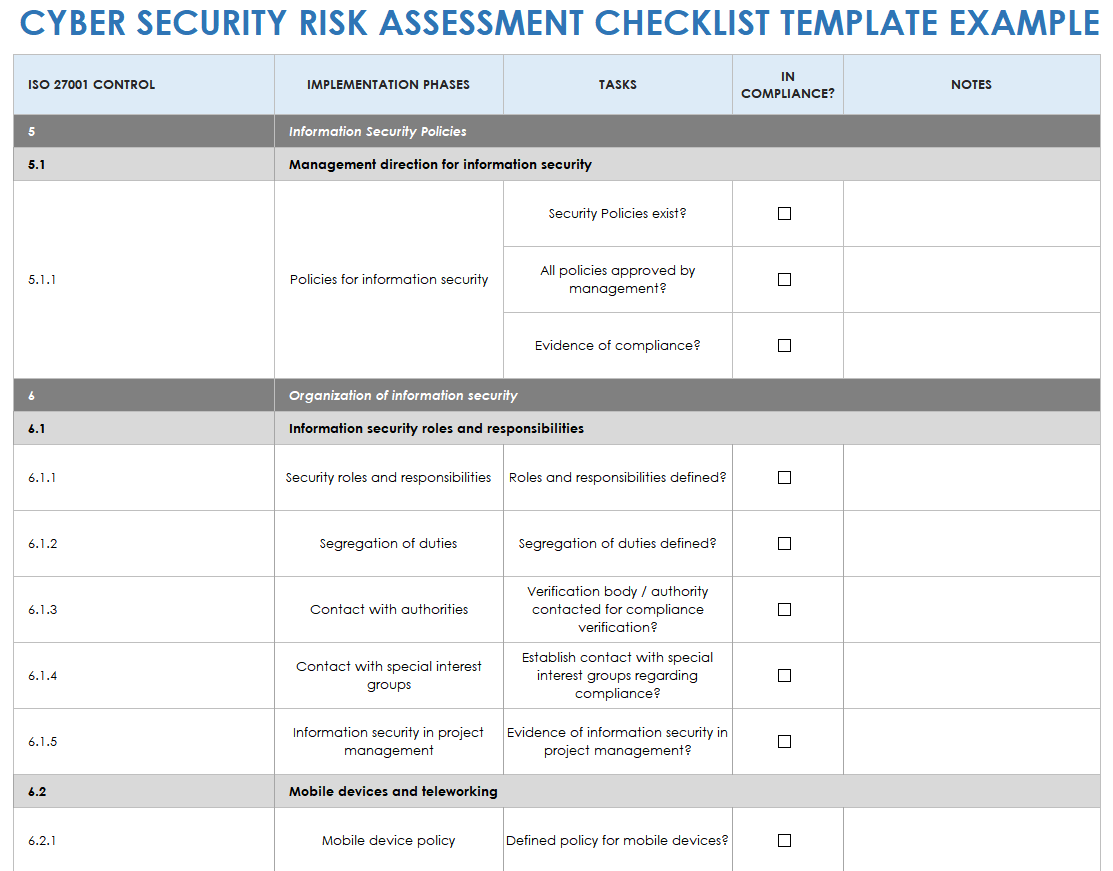
Cybersecurity Risk Assessment Chart For Organization | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

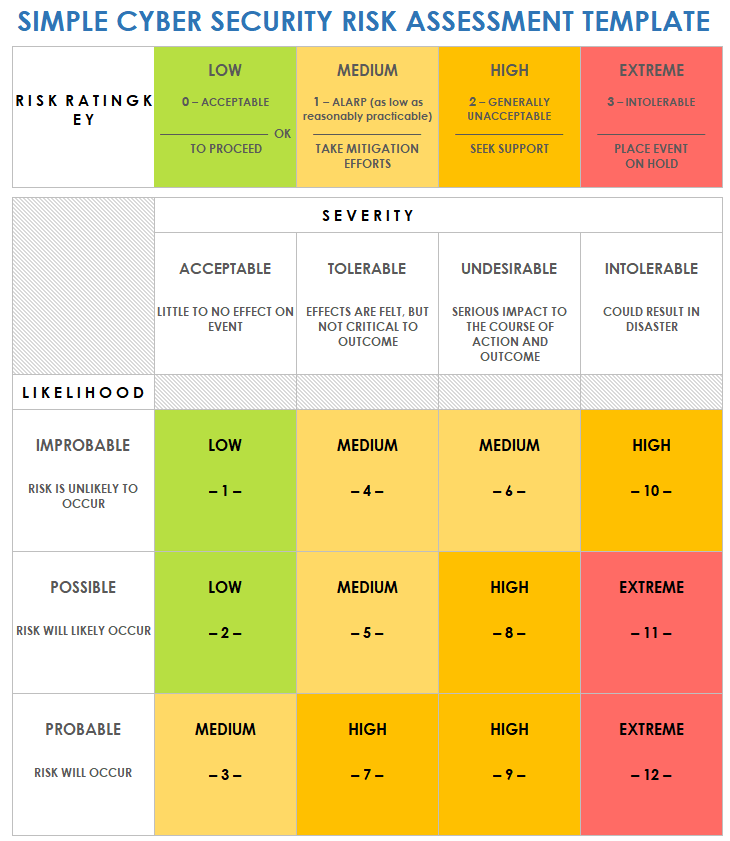
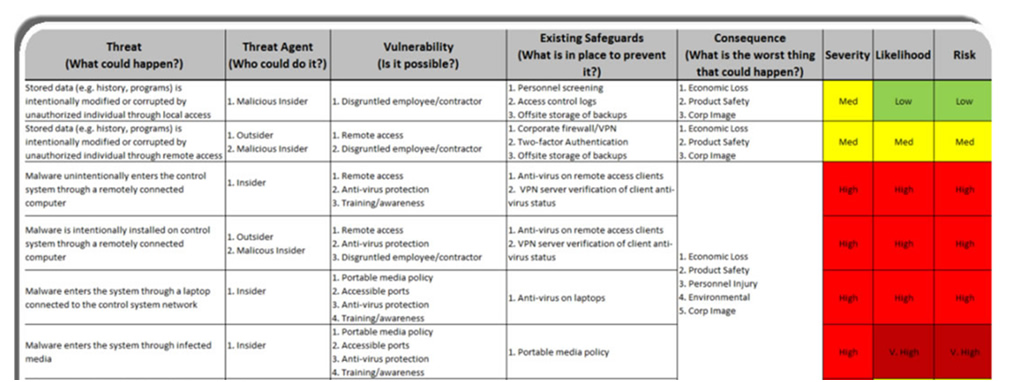
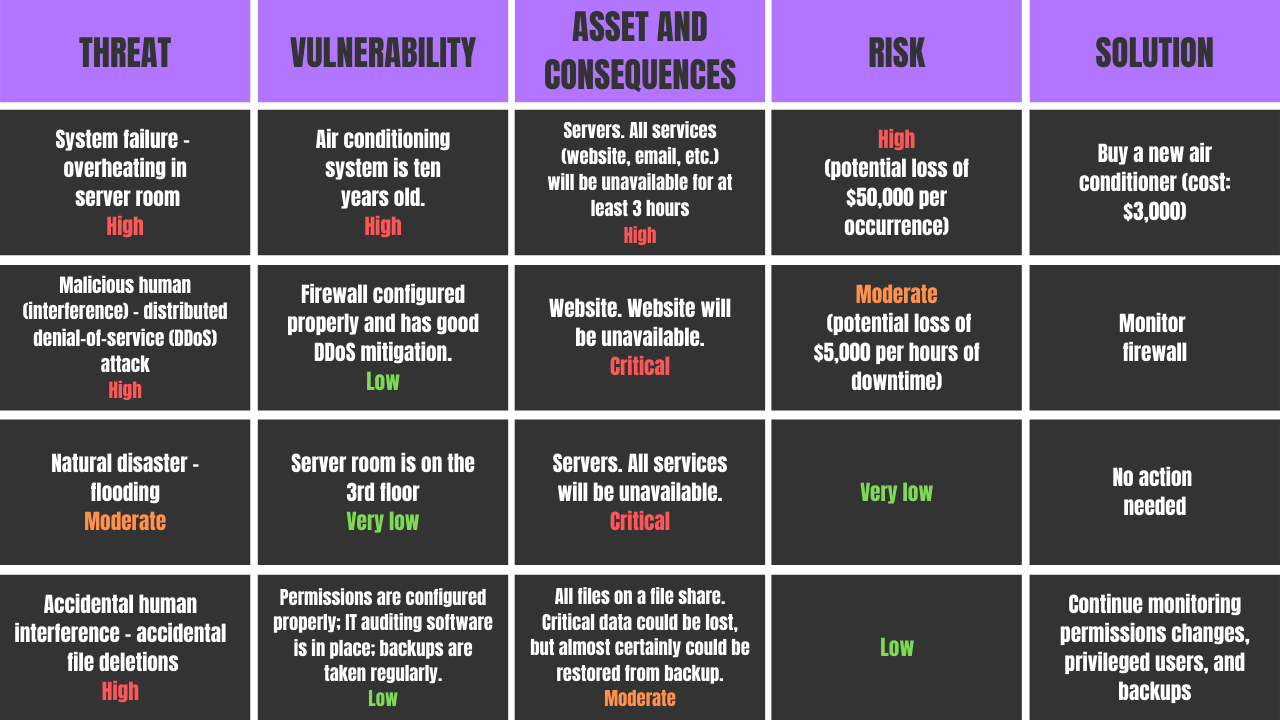
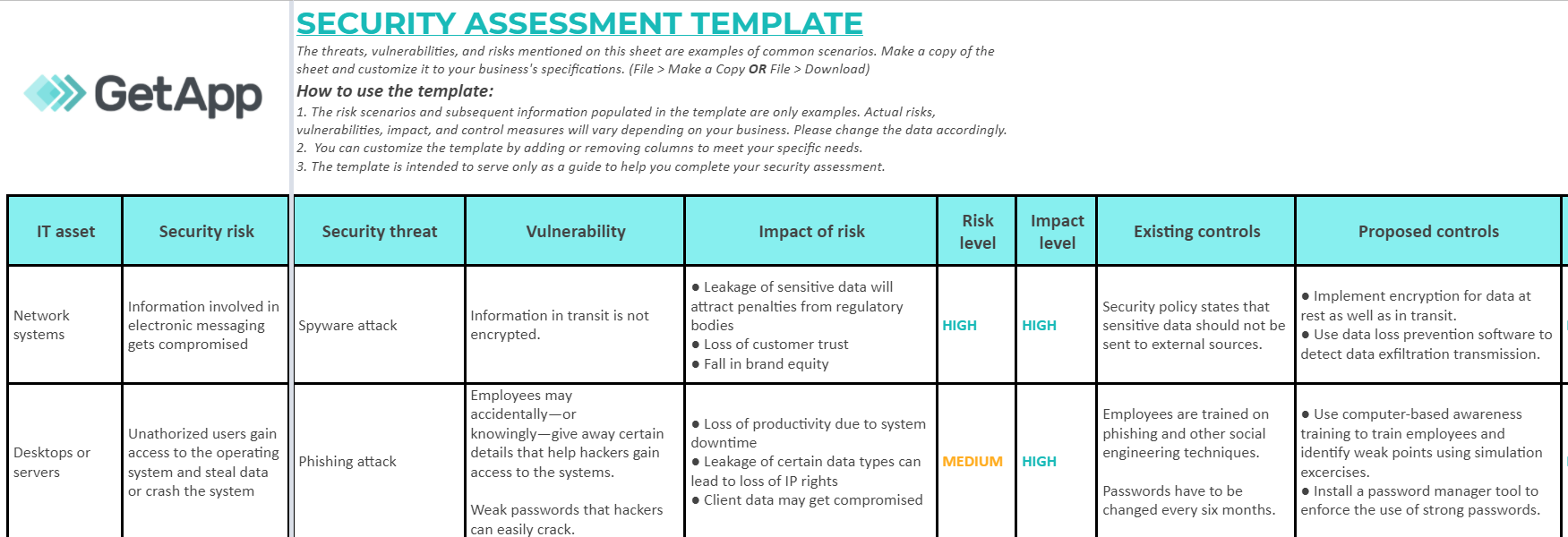
Cyber Security Risk Management Plan Information Security Risk Assessment Worksheet Consequences Diagrams PDF

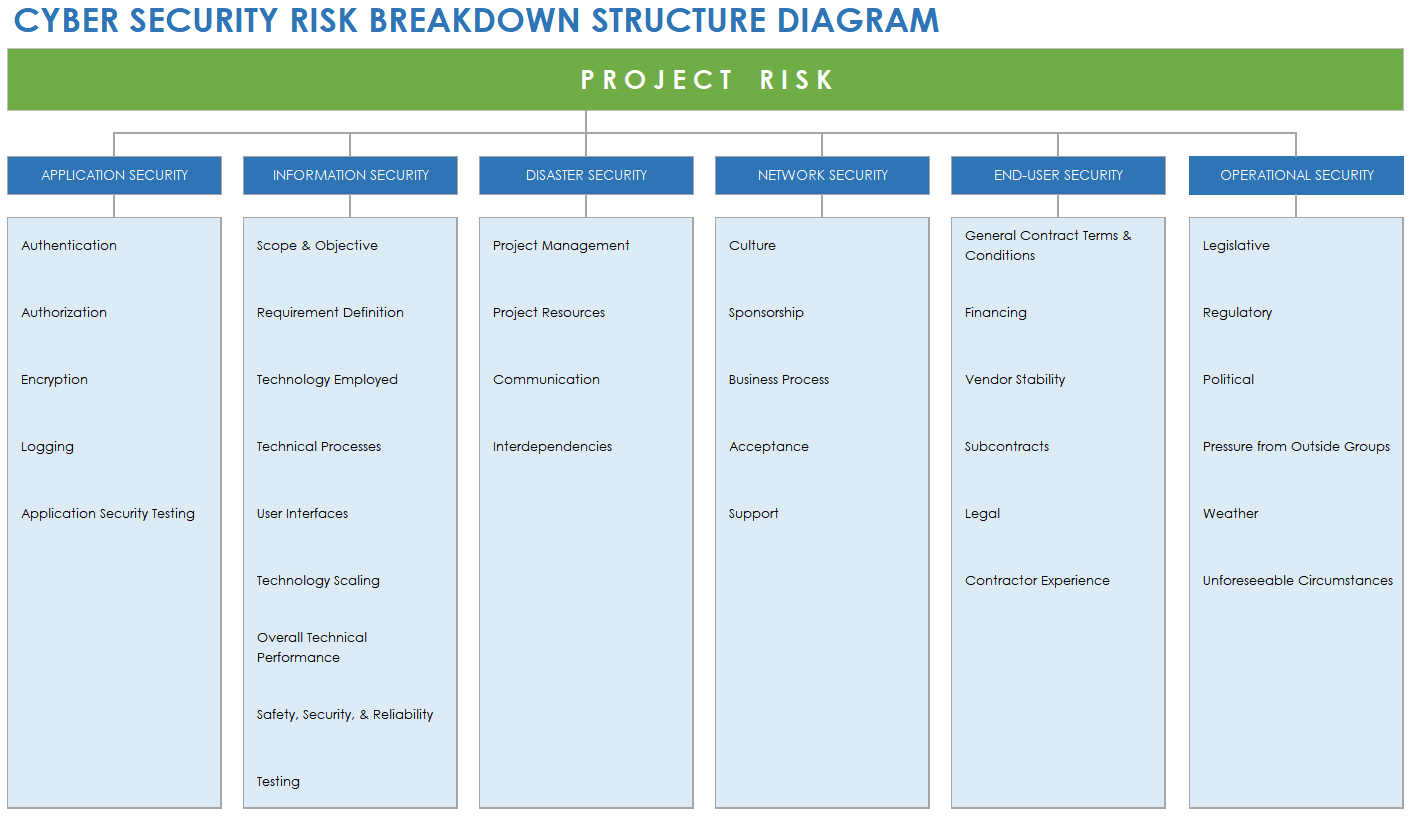
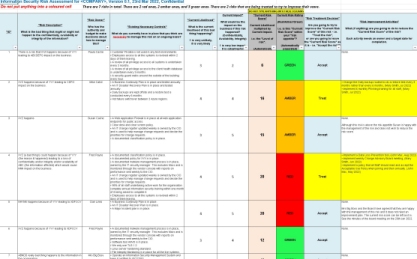
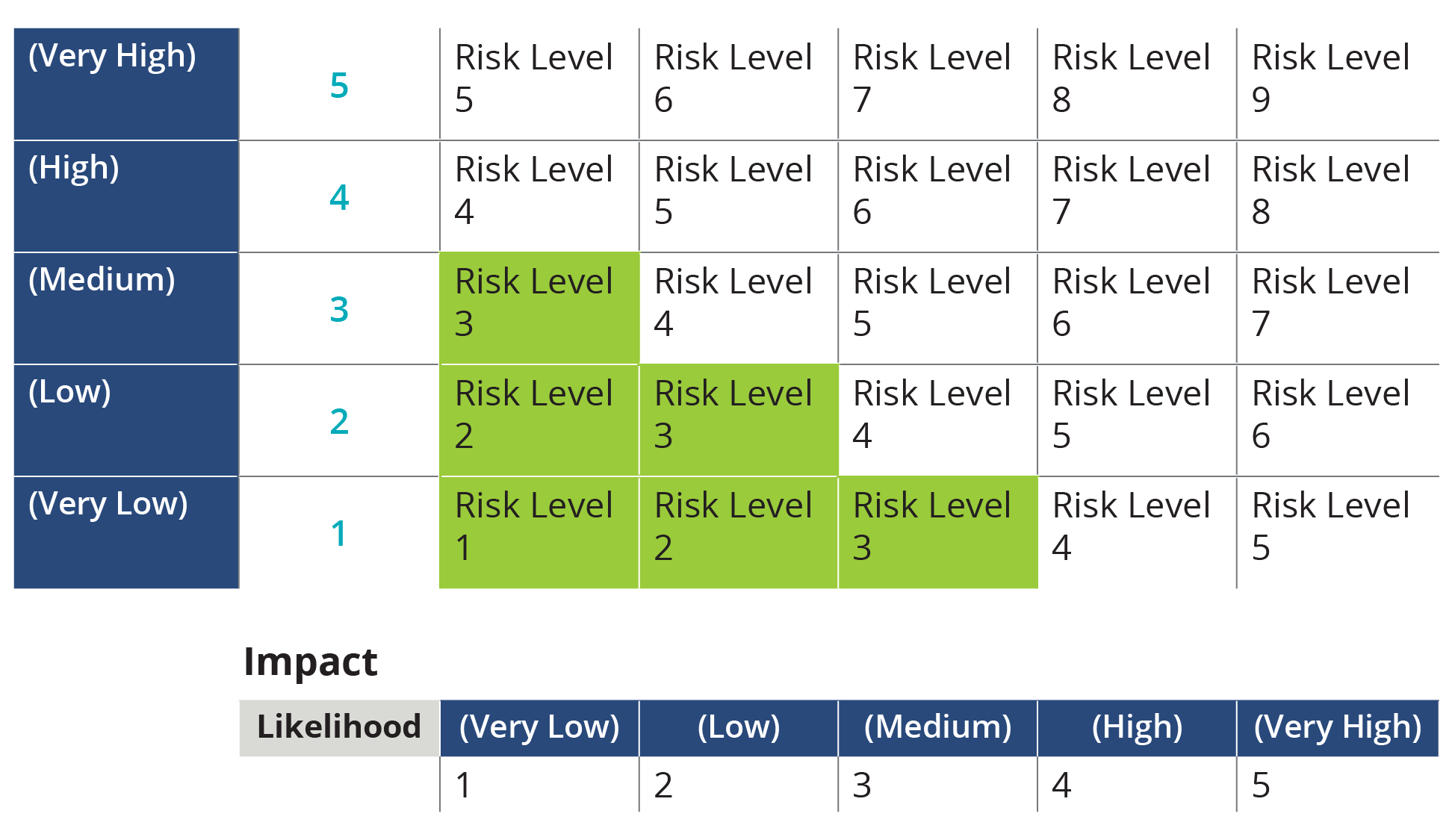
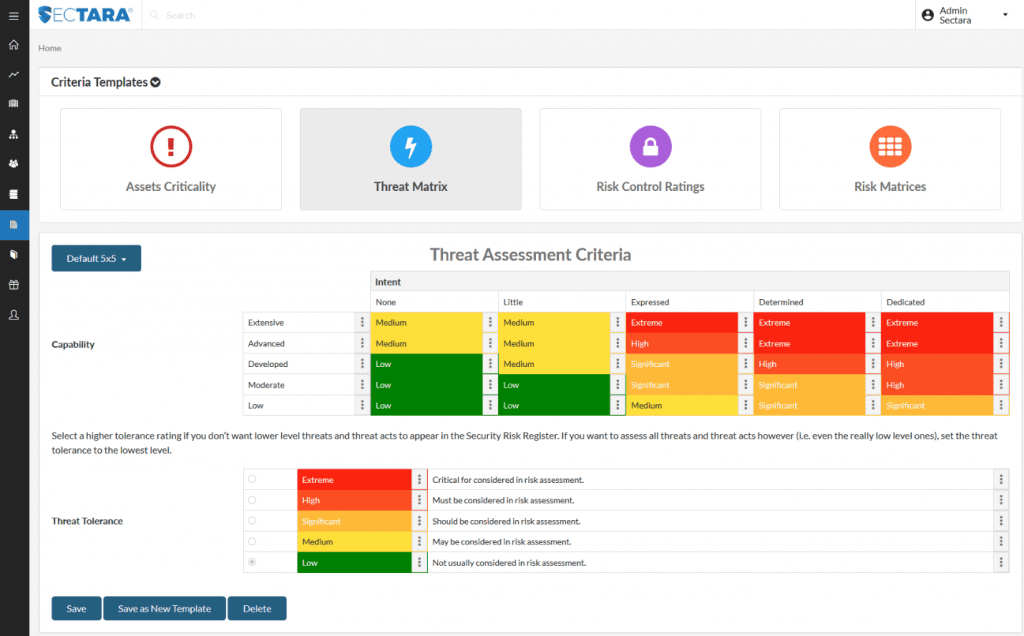
Information Security Risk Assessment Worksheet Level Ppt Styles Example | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

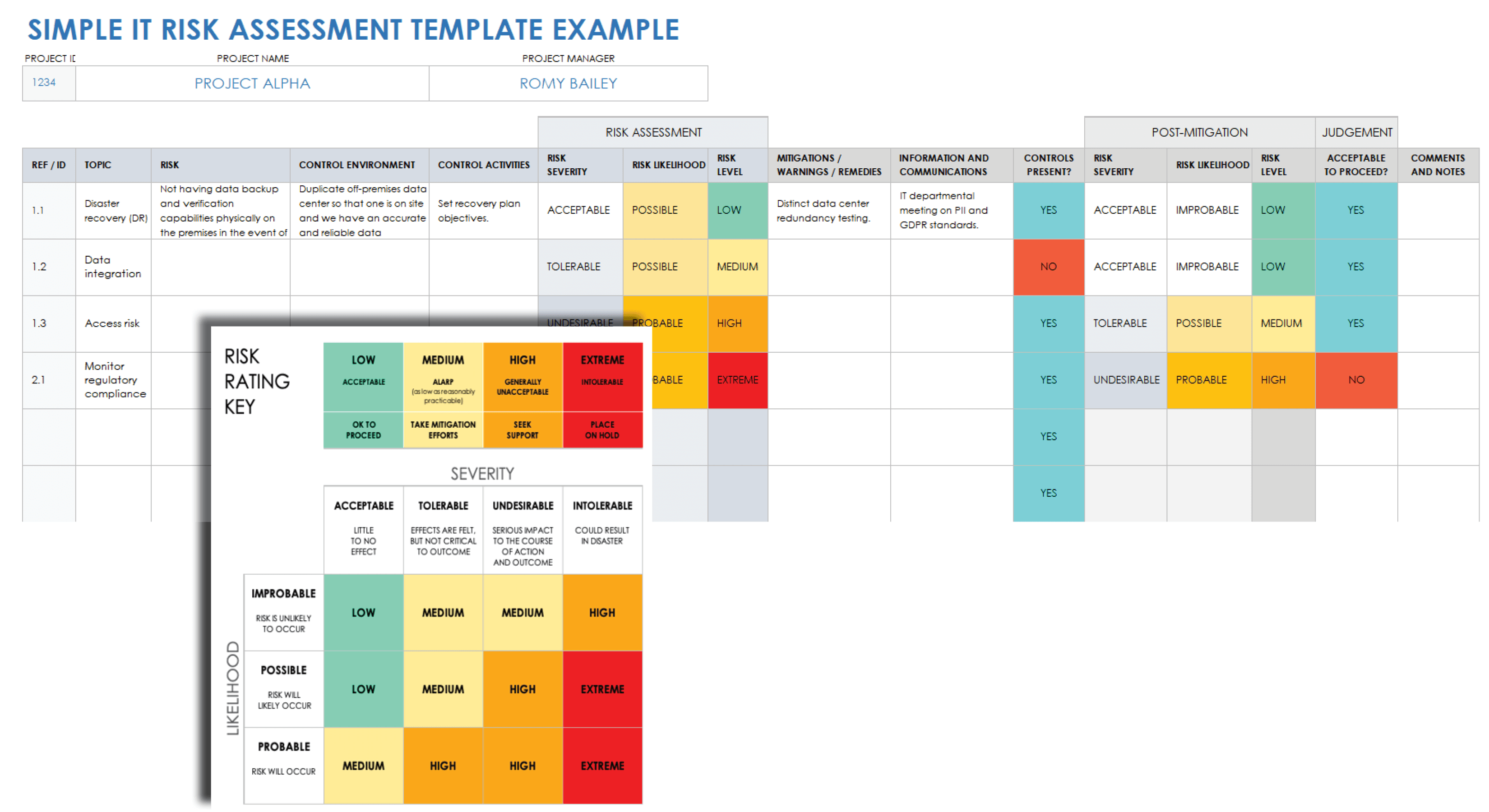
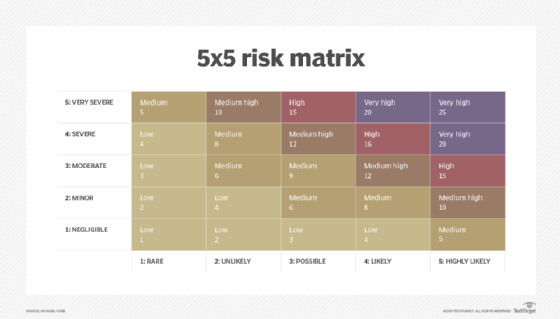
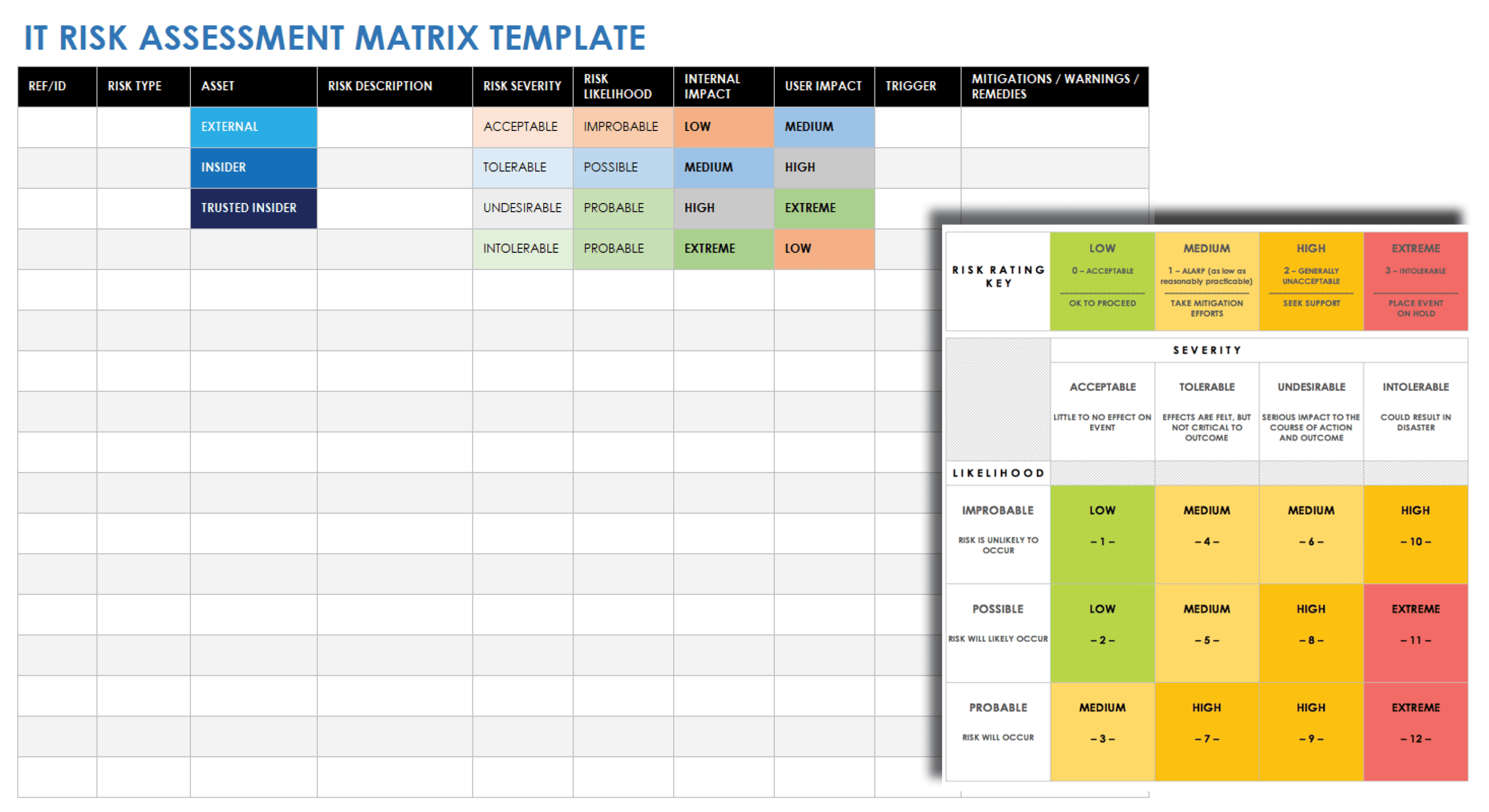
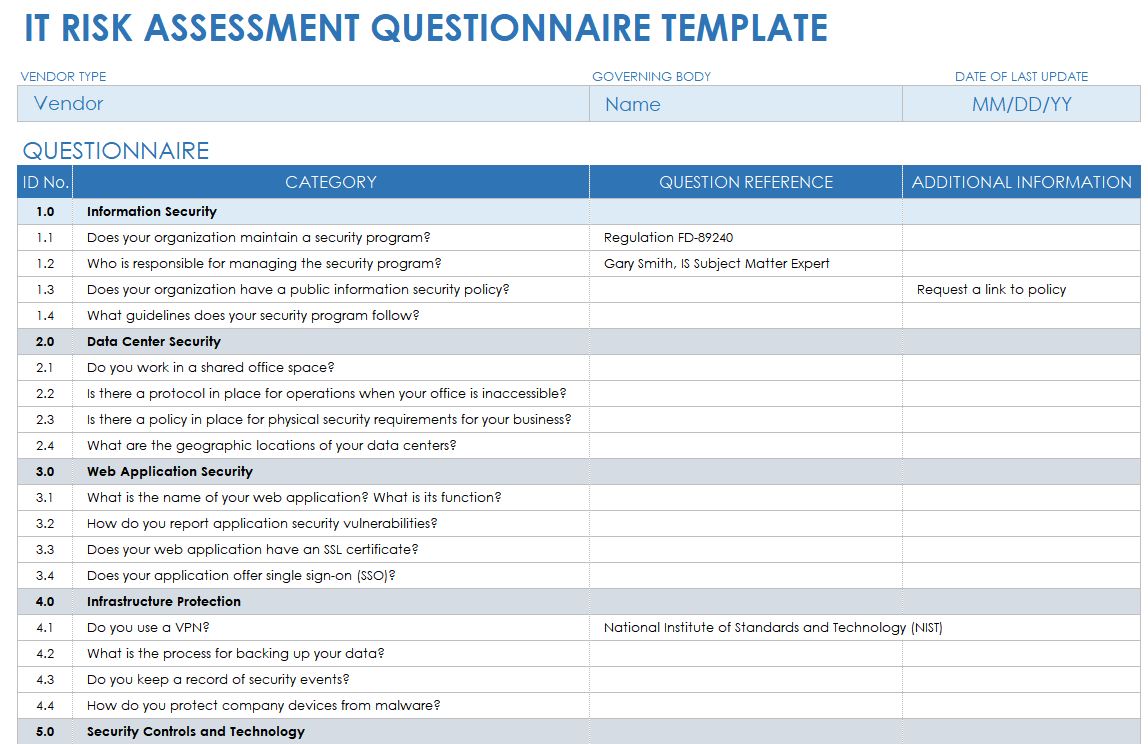
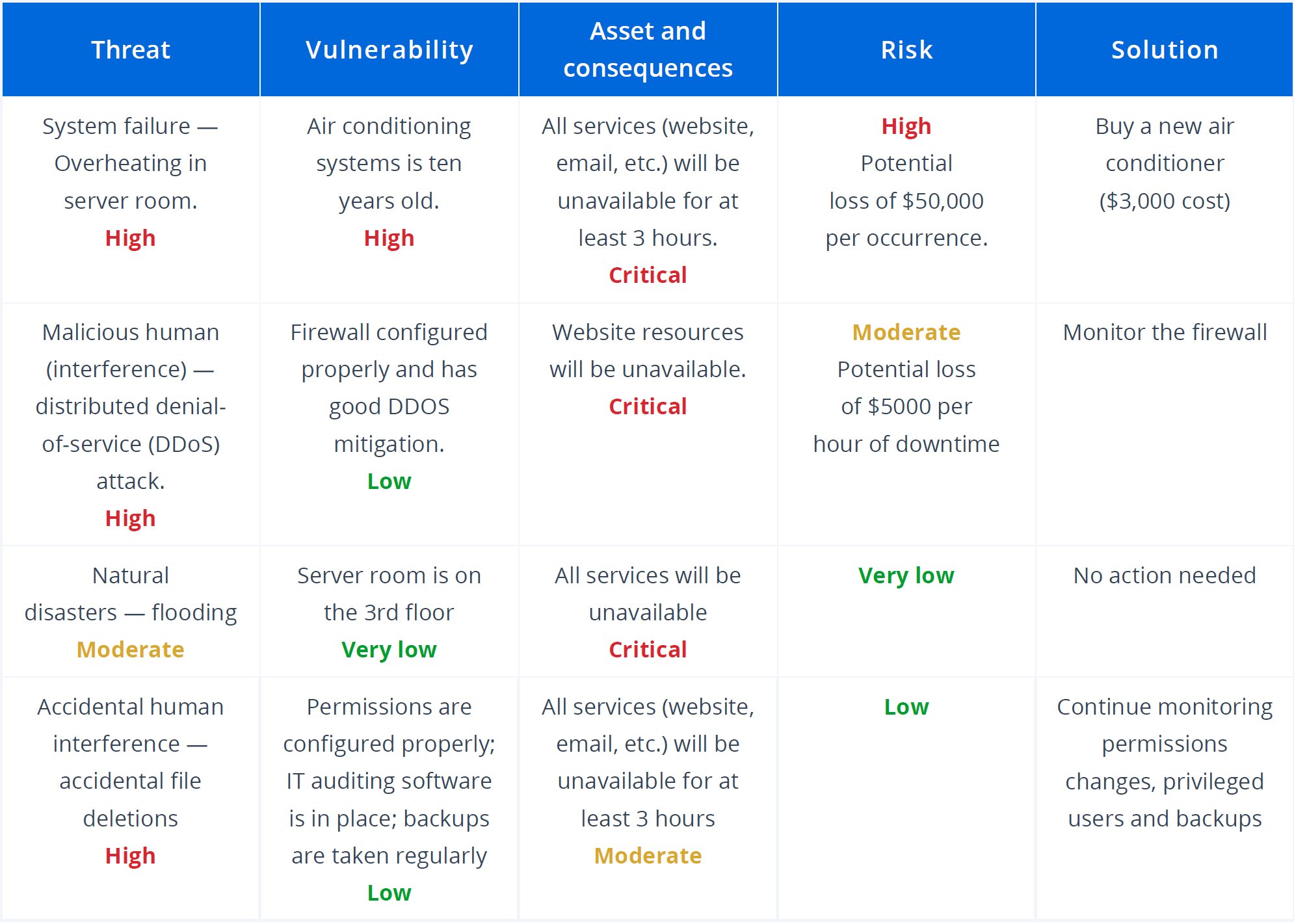
Security Risk assessment Template Lovely Security Risk assessment Template Excel Euthanasiapaper | Mission statement template, Assessment, Risk matrix